The threat of phishing attacks has become increasingly sophisticated, with Adversary-in-the-middle (AiTM) phishing kits now being a common trend observed to replace other less advanced forms of phishing. AiTM phishing can circumvent multifactor authentication (MFA) through its reverse-proxy functionality, and one notable actor is DEV-1101, a group tracked by Microsoft who is responsible for developing, supporting, and advertising several AiTM phishing kits. These kits are available for purchase or rent by other cybercriminals, which lowers the barrier to entry for cybercrime. The kit has been used in many phishing campaigns with varying motives and targets across various industries and sectors.
 |
| DEV-1101 increased their prices repeatedly due to rapid growth, Image: Microsoft |
DEV-1101 began advertising its AiTM kit around May 2022 through a Telegram channel and an advertisement in exploit[.]in, a popular cybercrime forum. The group increased the price of its tool multiple times due to the rapid growth of its user base from July through December 2022. As of now, the kit costs $300, with VIP licenses costing $1,000. Microsoft has detected many high-volume phishing campaigns from various actors using the kit offered by DEV-1101, comprising millions of phishing emails per day.
 |
| Malicious link shared in a phishing message for an AiTM campaign, Image: Microsoft |
While clicking the malicious link in the phishing message may result in two different evasions, the DEV-1101 kit's antibot functionality might trigger an href redirection to a benign page. This redirection domain is defined in the source code and could be different for each actor using the kit.
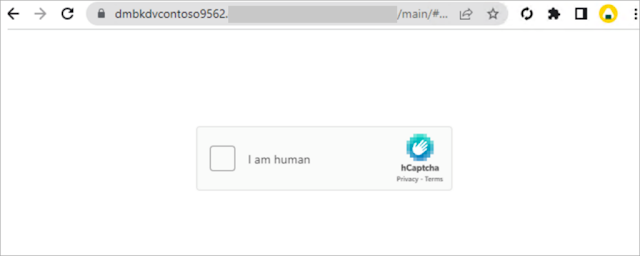 |
| Evasion through CAPTCHA page, Image: Microsoft |
The kit also allows threat actors to use CAPTCHA to evade detection. However, Microsoft 365 Defender can detect suspicious activities related to AiTM phishing attacks and follow-on activities, such as session cookie theft and attempts to use the stolen cookies to sign in.
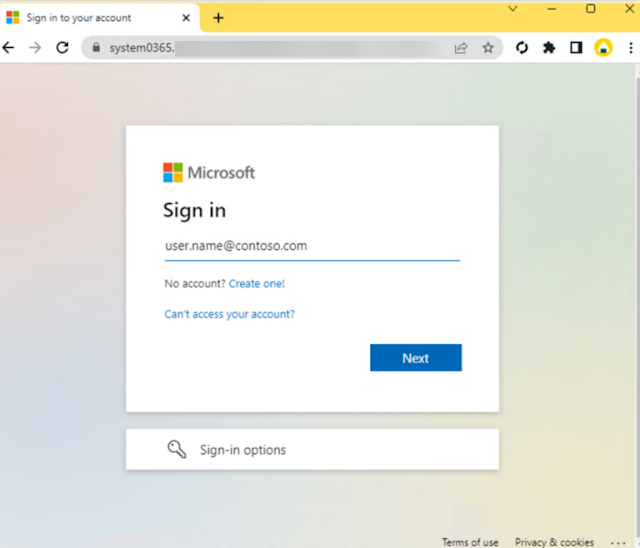 |
| Credential harvester mimicking a Microsoft sign-in portal, Image: Microsoft |
To prevent AiTM phishing attacks, Microsoft recommends that organizations take the following measures:
- Educate employees about AiTM phishing attacks and how to identify them.
- Encourage employees to use strong, unique passwords and to enable MFA wherever possible.
- Implement security solutions that can detect AiTM phishing attacks and follow-on activities.
- Regularly update software and systems to patch any vulnerabilities that could be exploited in AiTM phishing attacks.
- Monitor accounts for suspicious activity, such as logins from unfamiliar locations or devices.
- Block access to known malicious IP addresses and domains.
In conclusion, as cybercriminals continuously improve their tactics, the need for stronger cybersecurity measures is increasingly crucial. Organizations must be proactive in detecting and preventing AiTM phishing attacks to ensure their data remains secure.


0 Comments